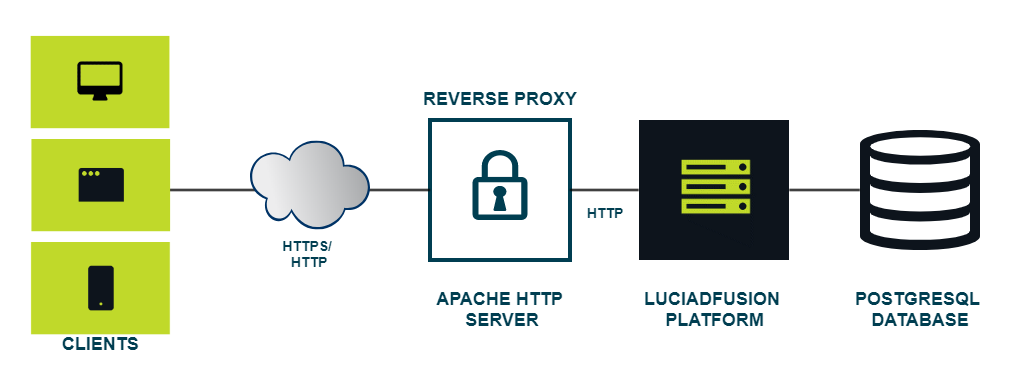
In this article we provide an example of how you can integrate the LuciadFusion Platform with an Apache HTTP server using a reverse proxy setup.
Why do it?
We recommend securing the LuciadFusion Platform by shielding it behind a web server like Apache HTTP Server with a reverse proxy setup. As a result, direct access to the LuciadFusion server is prohibited. In many organizations, such a setup is already in place. The reverse proxy setup makes the configuration of secured connections to the server easier. The client application uses HTTPS to communicate with the reverse proxy server, which forwards the requests to the LuciadFusion server using plain HTTP, on an internal network. The SSL certificates are managed by the reverse proxy server, the Apache HTTP Server in this case.
What do you need?
The steps below are based on using the following technologies:
-
LuciadFusion Platform.The LuciadFusion Platform v2017.0 or newer. The article instructions are intended for the standalone deployment version of the LuciadFusion Platform. A standalone LuciadFusion Platform deployment comes as a generated zip artifact with a start-up script and an embedded jetty servlet container.
-
Apache HTTP Server. These instructions are based on the use of the Apache HTTP Server 2.4. The provided configuration files have been tested with this version.
-
PostgreSQL database. The database back-end for the LuciadFusion Studio Service used here is PostgreSQL with the PostGIS extension.
How to do it?
Prepare the PostgreSQL database back-end
We create a user specifically for the LuciadFusion Studio database. Next, we create the Studio database and enable the PostGIS extension. You need to perform these initial steps as a PostgreSQL administrative user.
create role fusion_studio_admin with login password 'EDzRL2z3Toq9vXmU';
create database fusion_studio with owner fusion_studio_admin;
-- connect fusion_studio
create extension postgis;Create a deployment of the LuciadFusion Platform
|
In this article, it is assumed that the LuciadFusion server is used in a standalone deployment, with an embedded jetty server. |
The paths mentioned in this section are relative to the root directory of your LuciadFusion installation.
Install your deployment license
Copy your deployment license file deployment.jar into the folder licenses.
Install ProGuard
Install ProGuard by following the instructions in this article.
Configure a production profile
The profile configuration files are located in the folder config.
You configure a production profile by basing the file config/application-fusion.production.yml on the template configuration file application-fusion.production-template.yml, and adding the configuration items in this section to that configuration file.
You can find a complete configuration file at the end of this section.
The following configuration settings modify the default location of the service end points.
# Run the 'proxied' server application on port 8082 server.port: 8082 # Configure the context path of the LuciadFusion application server.servlet.context-path: /proxytest
These settings configure the LuciadFusion server for listening on port 8082, and make its end points available within the
context path proxytest.You must access them via http://localhost:8082/proxytest.
# We want to use this standalone server in a reverse-proxy setup. # As such, we need to configure the embedded (jetty) servlet container # to take the forward headers into account. server.forward-headers-strategy: native
The above setting configures the embedded jetty servlet container to take into account the headers provided by the Apache
HTTP server that is used as a reverse proxy. As a result, the OGC services can return end point URLs as they are seen from
the outside world. Without this setting, the end points would contain localhost as the server, and 8082 as the port, whereas the proxy server typically runs on port 80 for HTTP and 443 for HTTPS.
You can copy the file content provided here into the file config/application-fusion.production.yml.It contains a complete production profile configuration.
LuciadFusion production profile for reverse proxy test setup
######################
# Production profile #
######################
# Production profile that should be used when deploying the Fusion Platform server.
# This profile must be combined with the "fusion.single" profile as active profile.
# For example by using a vm property:
# -Dspring.profiles.active=fusion.single,fusion.production
# or a program argument:
# --spring.profiles.active=fusion.single,fusion.production
# This profile requires additional configuration before being ready for use.
# At least the following properties need to be modified or set:
# - fusion.security.cors.origins
# - fusion.security.authenticationManager
# - fusion.security.authenticationTypes
# - fusion.studio.configuration.datastore
# - fusion.studio.db.server
# - fusion.studio.db.port
# - fusion.studio.db.username
# - fusion.studio.db.password
# - fusion.engine.tilestoreHome
# An important property that can't be set through a profile specific property
# is the java heap space.
# It can be set in the options file
# config/vmoptions/com.luciad.fusion.platform.vmoptions
# Also see the LuciadFusion deployment guide for more information.
###################
# Shared settings #
###################
# Includes all configuration properties that are shared between all used configuration files.
# Make sure not to duplicate any properties from the fusion.common.yml configuration in this
# file to change them, but
# - either modify them in the fusion.common.yml configuration file
# - or copy the property to the fusion.development and fusion.production profiles if
# you want to use different values for development and production
spring.config.import: classpath:fusion.common.yml
####################
# General settings #
####################
# In order to change the port in which LuciadFusion Platform runs,
# refer to the documentation of the servlet container,
# for example Apache Tomcat or Jetty.
# Run the 'proxied' server application on port 8082
server.port: 8082
# We want to use this standalone server in a reverse-proxy setup.
# As such we need to configure the embedded (jetty) serlet container we
# want to take the forward headers into account.
server.forward-headers-strategy: native
# Configure the context path of the LuciadFusion application
server.servlet.context-path: /proxytest
# Determines which file is used to configure logging. Adjust/replace this file to modify the log levels / log file location.
logging:
config: classpath:fusion.logback.xml
# Used by fusion.logback.xml and the logfile actuator (http://host:port/{contextPath}/actuators/logfile)
file.name: logs/fusion.log
###############################
# General settings (security) #
###############################
fusion.security:
# Enables built-in security.
# If built-in security is disabled, the spring default security settings are used.
# Then you need to plug in your own security configuration into spring.
enabled: true
# CORS (Cross-origin resource sharing) configuration.
# A list of origins for which cross-origin requests are allowed. Values may be:
# * a specific domain, e.g. "https://domain1.com"
# * the CORS defined special value "*" for all origins.
# * more flexible origins patterns with "*" anywhere in the host name in addition to port lists. Examples:
# - https://*.domain1.com -- domains ending with domain1.com
# - https://*.domain1.com:[8080,8081] -- domains ending with domain1.com on port 8080 or port 8081
# - https://*.domain1.com:[*] -- domains ending with domain1.com on any port, including the default port
cors.origins: '*'
# Select the built-in authentication manager to use
# (mandatory if fusion.security.enabled == true). One of:
# * authenticate_all: all users are authenticated
# * properties_in_memory: authentication is configured in this yml file
# (see application-fusion.development.yml for an example).
# * ldap_ad: LDAP Active Directory.
# * ldap: LDAP
authenticationManager: properties_in_memory
# Select the built-in authentication types to use
# (mandatory if fusion.security.enabled == true).
# One or more of:
# * http_basic: Configures HTTP Basic authentication.
# * form: Configures form authentication
authenticationTypes:
- http_basic
- form
###################################################################################
#
# Active Directory --- when ldap_ad is selected as authenticationManager
#
###################################################################################
#fusion:
# security:
# ldap_ad:
# domain: ad.example.com # required
# url: ldaps://dc-be.example.com # required
# rootDn: dc=ad,dc=example,dc=com # required
# searchFilter: # default value= (&(objectClass=user)(userPrincipalName={0}))
###################################################################################
#
# LDAP --- when ldapd is selected as authenticationManager
#
###################################################################################
#fusion:
# security:
# ldap:
# userSearch:
# base: cn=Users # the base suffix from which the user search should origin
# filter: '(&(objectClass=person)(uid={0}))' # filter that searches users
# groupSearch:
# base: ou=Groups # the base suffix from which the group search should origin
# filter: '(&(objectClass=group)(member={0}))' # filter that searches the LDAP groups the user belongs to
# attribute: cn # attribute from the found LDAP group(s) for which the value is returned by the search
#spring:
# ldap: # Ldap properties exposed by Spring Boot Ldap
# urls: ldaps://dc.example.com
# base: dc=ad,dc=example,dc=com
# username: 'cn=System Account,cn=Users,dc=ad,dc=example,dc=com'
# username: 'SystemAccount@ad.example.com'
# password: xxx
###################################################################################
#
# Simple in-memory --- when properties_in_memory is selected as authenticationManager
#
# Security configuration containing an 'admin' and 'dm' user.
# Not recommended for production.
#
###################################################################################
fusion:
security:
users:
- username: admin
password: eEKuwzjoggh89sTe
roles:
- ADMIN
# - username: dm
# password: dm
# roles:
# - DATA_MANAGER
#######################################
# Spring Boot Actuators Configuration #
#######################################
#
# Spring Boot Actuator allows you to to monitor to Studio running in production
# and gather information from it.
# It consists of HTTP or JMX endpoints. In addition to built-in endpoints,
# Studio has its own custom endpoints to provide some more information about the
# running application.
#
# For more information about the endpoints, please refer to Spring Reference Documentation :
# https://docs.spring.io/spring-boot/3.4.2/reference/actuator/endpoints.html
#
# In production environment, we recommend to disable built-in endpoints and enable
# the custom ones only
#
management:
# Exposes only the endpoints which are used in Studio
endpoints.web.exposure.include: 'health,logfilesize,logfile,systemStatusInfo,configurationInfo'
###################
# Studio settings #
###################
fusion.studio.configuration:
#
# Use this configuration to set the base path where Studio will save its data
# This includes: uploaded files, indexes, database files
# (in case you use embedded H2 database)
#
# Studio will try to create the folder and all its parent folders
# automatically in case they do not exist
#
# example value:
# datastore: /var/lib/luciadfusion_studio/datastore
# datastore: d:/luciadfusion_studio/datastore
# datastore: "${user.home}/local/luciadfusion_studio/datastore"
#
datastore:
#
# Pointers to files that Studio will use as default data during previews
#
defaultData:
#
# Studio will use the defaultBackgroundData file as background in the previews
# this file can be adjusted at runtime in the Map Preview section of the Settings page
#
# example value:
# defaultBackgroundData: ${fusion.engine.tilestoreHome}/Coverages/earth__image__hdr.xml
#
defaultBackgroundData:
#
# Studio will use the defaultRasterData file when previewing raster styles
# this file cannot be adjusted at runtime
#
# example value:
# defaultRasterData: Data/Dted/Alps/dmed
#
defaultRasterData:
#
# Studio will use the defaultVectorData file when previewing vector styles
# this file cannot be adjusted at runtime
#
# example value:
# defaultVectorData: Data/geojson/city.json
#
defaultVectorData:
#
# Default values to be used when auto-generating metadata files
# These values are all required in ISO 19115 metadata
# These values will be used if no value was found in the crawled metadata xml
# and no appropriate value could be auto-generated based on the data file
#
defaultMetadata:
#
# The language code of the language that the dataset is in (e.g. en, nl, fr, etc)
#
language:
#
# Default abstract text to be used
#
abstractText:
#
# Identification of, and means of communication with, person(s) and
# organisations associated with the dataset
#
responsibleParty:
#
# Function performed by the responsible party.
# possible values: resourceProvider, custodian, owner, user, distributor,
# originator, pointOfContact, principalInvestigator, processor, publisher, author
#
role:
#
# Name of the organisation of the responsible party
#
organisationName:
#
# List of emails to communicate with, person(s) and organisations
# associated with the dataset
#
# example values:
# email:
# - contact@organisation.com
# email:
# - contact.1 [at] organisation.com
# - contact.2 [at] organisation.com
#
email:
###################################################################################
#
# Studio Web Front End Settings
#
###################################################################################
fusion.studio.webapp:
# Configures the caching for resources shared over LuciadFusion Studio web front end.
# Configurations related to caching will be added to Cache-Control header of HTTP
# responses prepared by LuciadFusion Studio.
# In a production environment, we strongly recommend you to enable caching.
cache:
# Enabled or disables caching.
enabled: true
# The time period (in seconds) that determines how long the resources will be cached.
# 8640000 seconds = 100 days
maxAge: 8640000
# Configures the Studio web front end customization
theme:
# Enables or disables customization of the Studio web front end.
# enabled: false
#
# Enables or disables the theme configuration's auto reloading.
# If enabled, the theme configuration file will be monitored for changes
# and the webapp will be automatically reloaded to reflect these changes.
# In a production environment, we recommend disabling auto reloading. If you
# really want to enable it, you should consider defining a triggerPeriod as well.
# For more information, please refer to the development profile.
#
autoReloadingOnChange:
enabled: false
###################################################################################
#
# Supported databases: PostgreSQL, h2
#
###################################################################################
###################################################################################
# PostgreSQL connection template. RECOMMENDED DB for production!
# Assumes a database with name fusion_studio is available on localhost on port 5432
#
# Requires jdbc connection setting to the database server.
# url: jdbc:postgresql://localhost:5432/fusion_studio
# url: jdbc:postgresql://my.database.com:5432/fusion_studio
#
# The login credentials of the database.
# It is important that the database user has necessary grants to create schemas,
# tables and indexes the first time you run studio.
# You can use a user with less prvileges the subsequent times you run studio.
#
###################################################################################
db:
url: jdbc:postgresql://localhost:5432/fusion_studio
username: fusion_studio_admin
password: EDzRL2z3Toq9vXmU
###################################################################################
# H2 connection template.
#
# Requires jdbc connection setting to the database server.
# url: jdbc:h2:tcp://my.database.com:5432/~/fusion_studio
# url: jdbc:h2:mem:fusion_studio_inmemory
###################################################################################
# db:
# url: "jdbc:h2:${user.home}/local/luciadfusion_studio/core"
# username: fusion_studio_admin
# password: fusion_studio_admin
###########################
# Tiling service settings #
###########################
# Service that can be used for tiling data using the LTS/LFS protocols.
fusion.engine:
# Location of the tile store. This property is mandatory, unless the fusion tiling
# service is disabled (see fusion.engine.enabled property in
# fusion.common.yml).
# This value is set to a location inside
# the upload folder. The upload path is a location inside the datastore location
# (see fusion.studio.configuration.datastore property).
tilestoreHome: "${fusion.studio.configuration.datastore}/FusionCoverages"
################################
# OGC service base URL setting #
################################
# OGC services
# Defines the base URL to determine the advertised URLs of the OGC web service
# requests in the capabilities.
# By default, the advertised URLs are automatically determined based on the
# incoming request.
# In some cases (e.g., a proxy server setup in which the Host information is
# not forwarded), it can be necessary to manually set the web service request URL.
# Through the baseUrl parameter, the base URL of each OGC web service can be
# customized by replacing one or more variables in the following String pattern with
# a custom value:
# ${server.address}:${server.port}/${fusion.ogc.wms.basePath}/${instanceId}
#fusion.ogc:
# wms.baseUrl: "${server.address}:${server.port}/${fusion.ogc.wms.basePath}/${instanceId}"
# wfs.baseUrl: "${server.address}:${server.port}/${fusion.ogc.wfs.basePath}/${instanceId}"
# wcs.baseUrl: "${server.address}:${server.port}/${fusion.ogc.wcs.basePath}/${instanceId}"
# wmts.baseUrl: "${server.address}:${server.port}/${fusion.ogc.wmts.basePath}/${instanceId}"
# csw.baseUrl: "${server.address}:${server.port}/${fusion.ogc.csw.basePath}/${instanceId}"
#######################################
# REST API settings #
#######################################
fusion.studio.rest:
# Controls whether the http://host:port/api/specification endpoint will be exposed.
# This endpoint exposes the OpenAPI 3 specification for the server's rest api.
#apiSpecificationEnabled: true
# Controls whether the http://host:port/api/console endpoint will be exposed. This
# endpoint provides an interactive console use to document and experiment with the
# rest apis. Note that this interactive console requires apiSpecificationEnabled
# to be true.
#apiConsoleEnabled: true
# Controls whether the http://host:port/api/documentation endpoint will be exposed.
# This endpoint exposes the rest api development guide.
#developerGuideEnabled: true
Build the LuciadFusion server application for deployment
Run the deployment build script deploy_fusionplatform_service located in the folder build/fusionplatform.
Run the LuciadFusion server
Extract the generated zip artifact distrib/FusionPlatform/LuciadFusionPlatform_x.x.x/LuciadFusionPlatform.zip. You can now start the LuciadFusion server with StartFusionPlatformServer.
Configure the LuciadFusion server to serve data
Use LuciadFusion Studio to configure a WMS service end point, with the name background for example. Open the page http://localhost:8082/proxytest/studio/index.html to start the configuration. When you have configured a few products to be served through WMS, you can retrieve the WMS capabilities
using http://localhost:8082/proxytest/ogc/wms/background?service=WMS&request=GetCapabilities.
How to use Apache HTTP server as reverse proxy
Consult the Apache documentation
For more information about Apache HTTP server, see https://httpd.apache.org/docs/2.4/.
Set up a fictitious server name
While we are configuring the Apache HTTP Server as reverse proxy, we use the fictitious server name test-proxy.example.com. You need to configure your computer to recognize this server name, and map it onto your own machine.
For this reason, you need to update the hosts file by adding the following entry:
127.0.0.1 test-proxy.example.com
|
Host file location
|
Locate configuration files for Apache HTTP server
The location of the configuration files depends on the platform you are using. Have a look at the Platform Specific Notes section at https://httpd.apache.org/docs/2.4/ for your platform.
You can copy the content of the configuration samples below in a file test-proxy.conf within the configuration folder for Apache HTTP server.
In the following sections, we start with the configuration for HTTP connections. Next, we add the configuration for HTTPS connections. Note that for this example, we use a self-signed certificate for HTTPS.
|
In this article, we use a self-signed SSL certificate because most users won’t have access to an official certificate. You must not use a self-signed certificate in an actual production environment. Browsers block self-signed certificates by default, and you will have to allow exceptions to get the server response. |
Configure HTTP connections
The configuration example below shows the configuration of a virtual host within the Apache HTTP server. Request paths for
test-proxy.example.com are forwarded to the LuciadFusion server. The request paths for the Apache HTTP server and the LuciadFusion server are the
same.
Within the configuration, we do not expose the end points for the LuciadFusion Studio Service. The Studio Service requires a login with user credentials to prevent anyone from changing the server data configuration. We do not want to send the password in clear text over an unprotected connection.
Virtual host configuration for port 80 to LuciadFusion server on 8082
<VirtualHost *:80> ServerName test-proxy.example.com ProxyPass /proxytest/lts http://localhost:8082/proxytest/lts ProxyPassReverse /proxytest/lts http://localhost:8082/proxytest/lts ProxyPass /proxytest/ogc http://localhost:8082/proxytest/ogc ProxyPassReverse /proxytest/ogc http://localhost:8082/proxytest/ogc ProxyPass /proxytest/file http://localhost:8082/proxytest/file ProxyPassReverse /proxytest/file http://localhost:8082/proxytest/file ProxyPass /proxytest/hspc http://localhost:8082/proxytest/hspc ProxyPassReverse /proxytest/hspc http://localhost:8082/proxytest/hspc ProxyPass /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles ProxyPassReverse /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles ProxyPass /proxytest/schemas http://localhost:8082/proxytest/schemas ProxyPassReverse /proxytest/schemas http://localhost:8082/proxytest/schemas </VirtualHost>
Using the configuration above, you should be able to perform the WMS GetCapabilities request using the following URL: http://test-proxy.example.com/proxytest/ogc/wms/background?service=WMS&request=GetCapabilities. The end points for `GetMap and GetFeatureInfo should refer to the test-proxy.example.com server.
configure HTTPS connections
The use of HTTPS requires an SSL certificate. For the fictitious server name, we create a self-signed certificate.
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout test-proxy.example.com.key -out test-proxy.example.com.crt
The main configuration distinctions for a reverse-proxy setup with HTTPS are the activation of the SSL engine within the Apache HTTP server, and the inclusion of a request header that specifies that the source request is done with HTTPS.
SSLEngine On SSLCertificateFile /etc/ssl/test-proxy.example.com.crt SSLCertificateKeyFile /etc/ssl/test-proxy.example.com.key RequestHeader set X-Forwarded-Proto "https"
|
Make sure that the path to your SSL certificates is correct. |
Here is a complete configuration for a virtual host on the standard HTTPS port. This configuration includes the end point for the LuciadFusion Studio Service. You can add this configuration within the configuration file you already have for plain HTTP.
Virtual host configuration for port 443 to LuciadFusion server on port 8082
<VirtualHost *:443> ServerName test-proxy.example.com SSLEngine On SSLCertificateFile /etc/ssl/test-proxy.example.com.crt SSLCertificateKeyFile /etc/ssl/test-proxy.example.com.key RequestHeader set X-Forwarded-Proto "https" ProxyPass /proxytest/lts http://localhost:8082/proxytest/lts ProxyPassReverse /proxytest/lts http://localhost:8082/proxytest/lts ProxyPass /proxytest/ogc http://localhost:8082/proxytest/ogc ProxyPassReverse /proxytest/ogc http://localhost:8082/proxytest/ogc ProxyPass /proxytest/file http://localhost:8082/proxytest/file ProxyPassReverse /proxytest/file http://localhost:8082/proxytest/file ProxyPass /proxytest/hspc http://localhost:8082/proxytest/hspc ProxyPassReverse /proxytest/hspc http://localhost:8082/proxytest/hspc ProxyPass /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles ProxyPassReverse /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles ProxyPass /proxytest/schemas http://localhost:8082/proxytest/schemas ProxyPassReverse /proxytest/schemas http://localhost:8082/proxytest/schemas ProxyPass /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications ProxyPassReverse /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications ProxyPass /proxytest/studio http://localhost:8082/proxytest/studio ProxyPassReverse /proxytest/studio http://localhost:8082/proxytest/studio ProxyPass /proxytest/actuators http://localhost:8082/proxytest/actuators ProxyPassReverse /proxytest/actuators http://localhost:8082/proxytest/actuators ProxyPass /proxytest/login http://localhost:8082/proxytest/login ProxyPassReverse /proxytest/login http://localhost:8082/proxytest/login ProxyPass /proxytest/api http://localhost:8082/proxytest/api ProxyPassReverse /proxytest/api http://localhost:8082/proxytest/api </VirtualHost>
Using the configuration above, you should be able to perform the WMS GetCapabilities request using the following URL: https://test-proxy.example.com/proxytest/ogc/wms/background?service=WMS&request=GetCapabilities. The end points for GetMap and GetFeatureInfo should refer to the test-proxy.example.com server with the HTTPS protocol.
Configuring for HTTP as well as HTTPS
You could also allow clients to use HTTP for the LuciadFusion Studio application, but re-direct them automatically to the HTTPS counterpart.
You can find the complete configuration file here:
Complete virtual host configuration
<VirtualHost *:80>
ServerName test-proxy.example.com
RewriteEngine On
# Force HTTPS for studio
RewriteCond %{HTTPS} off
RewriteCond %{THE_REQUEST} \s/proxytest/studio [NC]
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [NE,R=301,L]
#ErrorLog /var/log/httpd/test-proxy-error.log
#CustomLog /var/log/httpd/test-proxy-access.log common
ProxyPass /proxytest/lts http://localhost:8082/proxytest/lts
ProxyPassReverse /proxytest/lts http://localhost:8082/proxytest/lts
ProxyPass /proxytest/ogc http://localhost:8082/proxytest/ogc
ProxyPassReverse /proxytest/ogc http://localhost:8082/proxytest/ogc
ProxyPass /proxytest/file http://localhost:8082/proxytest/file
ProxyPassReverse /proxytest/file http://localhost:8082/proxytest/file
ProxyPass /proxytest/hspc http://localhost:8082/proxytest/hspc
ProxyPassReverse /proxytest/hspc http://localhost:8082/proxytest/hspc
ProxyPass /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles
ProxyPassReverse /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles
ProxyPass /proxytest/schemas http://localhost:8082/proxytest/schemas
ProxyPassReverse /proxytest/schemas http://localhost:8082/proxytest/schemas
ProxyPass /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications
ProxyPassReverse /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications
ProxyPass /proxytest/studio http://localhost:8082/proxytest/studio
ProxyPassReverse /proxytest/studio http://localhost:8082/proxytest/studio
ProxyPass /proxytest/actuators http://localhost:8082/proxytest/actuators
ProxyPassReverse /proxytest/actuators http://localhost:8082/proxytest/actuators
ProxyPass /proxytest/login http://localhost:8082/proxytest/login
ProxyPassReverse /proxytest/login http://localhost:8082/proxytest/login
ProxyPass /proxytest/api http://localhost:8082/proxytest/api
ProxyPassReverse /proxytest/api http://localhost:8082/proxytest/api
</VirtualHost>
<VirtualHost *:443>
ServerName test-proxy.example.com
SSLEngine On
SSLCertificateFile /etc/ssl/test-proxy.example.com.crt
SSLCertificateKeyFile /etc/ssl/test-proxy.example.com.key
RequestHeader set X-Forwarded-Proto "https"
#ErrorLog /var/log/httpd/test-proxy-error.log
#CustomLog /var/log/httpd/test-proxy-access.log common
ProxyPass /proxytest/lts http://localhost:8082/proxytest/lts
ProxyPassReverse /proxytest/lts http://localhost:8082/proxytest/lts
ProxyPass /proxytest/ogc http://localhost:8082/proxytest/ogc
ProxyPassReverse /proxytest/ogc http://localhost:8082/proxytest/ogc
ProxyPass /proxytest/file http://localhost:8082/proxytest/file
ProxyPassReverse /proxytest/file http://localhost:8082/proxytest/file
ProxyPass /proxytest/hspc http://localhost:8082/proxytest/hspc
ProxyPassReverse /proxytest/hspc http://localhost:8082/proxytest/hspc
ProxyPass /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles
ProxyPassReverse /proxytest/mbtiles http://localhost:8082/proxytest/mbtiles
ProxyPass /proxytest/schemas http://localhost:8082/proxytest/schemas
ProxyPassReverse /proxytest/schemas http://localhost:8082/proxytest/schemas
ProxyPass /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications
ProxyPassReverse /proxytest/studio/service/notifications ws://localhost:8082/proxytest/studio/service/notifications
ProxyPass /proxytest/studio http://localhost:8082/proxytest/studio
ProxyPassReverse /proxytest/studio http://localhost:8082/proxytest/studio
ProxyPass /proxytest/actuators http://localhost:8082/proxytest/actuators
ProxyPassReverse /proxytest/actuators http://localhost:8082/proxytest/actuators
ProxyPass /proxytest/login http://localhost:8082/proxytest/login
ProxyPassReverse /proxytest/login http://localhost:8082/proxytest/login
ProxyPass /proxytest/api http://localhost:8082/proxytest/api
ProxyPassReverse /proxytest/api http://localhost:8082/proxytest/api
</VirtualHost>
|
Make sure that the path to your SSL certificates is correct. |